An Enhanced Message Priority Mechanism in IEEE 802.11p Based Vehicular Networks
Article information
Abstract
IEEE 802.11p is a standard MAC protocol for wireless access in vehicular environments (WAVEs). If a packet collision happens when a safety message is sent out, IEEE 802.11p chooses a random back-off counter value in a fixed-size contention window. However, depending on the random choice of back-off counter value, it is still possible that less important messages are sent out first while more important messages are delayed longer until sent out. In this paper, we present a new scheme for safety message scheduling, called the enhanced message priority mechanism (EMPM). It consists of the following two components: the benefit-value algorithm, which calculates the priority of the messages depending on the speed, deceleration, and message lifetime; and the back-off counter selection algorithm, which chooses the non-uniform back-off counter value in order to reduce the collision probability and to enhance the throughput of the highly beneficial messages. Numerical results show that the EMPM can significantly improve the throughput and delay of messages with high benefits when compared with existing MAC protocols. Consequently, the EMPM can provide better QoS support for the more important and urgent messages.
1. Introduction
In recent years, many researchers have focused on the vehicular networks, which can improve the safety, the driving efficiency, and the convenience of driving by exchanging messages among the vehicles. They can be seen as an instance of mobile ad-hoc networks (MANETs), which consist of two pieces of equipment: the on-board unit (OBU) in a fast moving vehicle and the roadside unit (RSU) at a fixed point on the road. To disseminate messages in vehicular networks, an OBU aggregates information elements of the message, and then sends it to the other OBUs or the RSUs. The communication between two OBUs is called vehicle-to-vehicle (V2V) communication. On the other hand, the communication between the OBU and the RSU is called vehicle-to-infrastructure (V2I) communication.
In parallel with these activities, there are also many standardization efforts being carried out on vehicular networks (i.e., IEEE 1609.x [1–5] and IEEE 802.11p standards). To support service differentiation among multiple classes of traffic, the IEEE 802.11p standards adopt the enhanced distributed channel access (EDCA) in IEEE 802.11e. However, the EDCA does not take into account some realistic aspects of vehicular networks, such as speed, deceleration, and road environments, in the determination of the message priority. To resolve this problem, the works in [6–8] present a new framework to incorporate many realistic factors based on the benefit value. However, these works have two major problems: 1) they do not present how to define/use the benefit value in a practical vehicular network and 2) they choose a back-off counter value uniformly over a fixed interval [0, CW-1], where CW is the contention window size. These limitations result in an incomplete differentiation of the messages contending for the channel access, which may lead to a sizeable latency for the emergency messages.
In this paper, we propose a new enhanced message priority mechanism (EMPM), which can be decomposed into two parts: the benefit-value algorithm and the back-off counter selection algorithm. The benefit-value algorithm calculates the new priority measure for a message, named the benefit value, which reflects the context of vehicular environments, such as speed and deceleration. Based on the benefit value, the back-off counter selection algorithm determines the back-off counter value of IEEE 802.11p MAC. To support a better priority differentiation, the back-off counter selection algorithm employs the Poisson distribution, instead of the uniform distribution, to obtain the back-off counter value. The parameter of the Poisson distribution is set by a non-increasing function of the benefit value so that the emergency message is disseminated with only a small delay. The numerical results show that the EMPM can significantly reduce the delay of a high priority message, while the delay of low priority messages slightly increases.
The rest of this paper is organized as follows: in Section 2, some studies related to this topic are discussed. We introduce our proposed EMPM and its two major components in Section 3. The experimental results and some analyses are shown in Section 4. Finally, in Section 5, we present our conclusions and proposals for future work.
2. Related Work
2.1 WAVE Standards
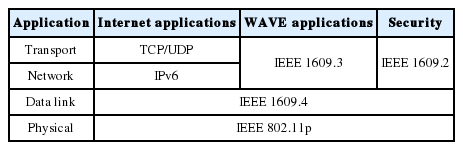
The WAVE standard suite defines the communication protocols between vehicles moving at a high speed on the road and between a vehicle and a roadside infrastructure. Table 1 shows the architecture of a WAVE standard suite, including IEEE 1609.x and IEEE 802.11p standards.
Table 1 shows the structure of the WAVE standard suite. The IEEE 802.11p focuses on the standardization of the physical and the MAC layers. To support multichannel operation, IEEE 1609.4 defines the channel switching at a 5.9-GHz dedicated short-range communications (DSRC) band. The WAVE standard supports a dual protocol suite on top of IEEE 1609.4. One is the TCP/IP protocol suite for Internet access applications and the other is the WAVE short message protocol (WSMP) for disseminating safety-critical messages. In addition, IEEE 1609.2 defines the security mechanism of the WAVE standard. In this paper, we will focus on the design of a new MAC protocol in the WAVE standard suite.
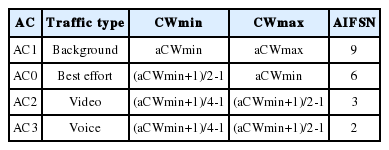
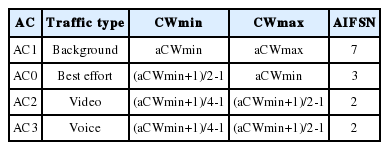
The EDCA is a mechanism to support the service differentiation of user traffic in the IEEE 802.11 MAC layer [9]. IEEE 802.11p employs the EDCA mechanism to prioritize many different kinds of traffic in vehicular networks. To achieve this goal, the EDCA controls the duration of the inter-frame spaces (IFSs) and the size of the CW for four access categories of user traffic, which are as follows: background, best effort, voice, and video traffic. The DSRC channels consist of one control channel (CCH) and six service channels (SCHs). Tables 2 and 3 show the IFS and CW sized parameters used to support four different access categories of the EDCA in CCH and in SCHs.
2.2 Related Works in Vehicular Networks
In vehicular networks, it is of utmost importance to support the QoS requirements of diverse applications. Most of the existing works extend the basic QoS mechanism in the IEEE 802.11e standard. In [10], the authors present the development of an analysis model, while also taking into account some new features of the EDCA, such as virtual collision, different arbitration inter frame spaces (AIFSs), and different CW sizes. The work in [11] investigates the impacts of back-off parameters, such as the minimum back-off window size, the back-off window-increasing factor, and the retransmission limit, on the performance of EDCA. In [12], the authors address the benefit of using the EDCA for better supporting the safety messages in vehicular ad-hoc networks.
In [6–8], the authors present a new mechanism to provide service differentiation based on the benefit value. In [7], the authors present a new definition called, ‘benefit value,’ and utilized the aggregated benefit values over all of the receiving nodes as a performance metric. In this scheme, the sending vehicle independently evaluates the benefit of the current packet before transmitting a message. According to the benefit value, the sending vehicle first calculates a local order of the messages in the sending queue. Next, either a proprietary cross-layer approach or the IEEE 802.11e QoS standard disseminates the benefit-based messages.
The authors of [7] presented a novel equation to calculate the benefit value based on the context information, which is:
Message context m can be characterized by the message age (i.e., the time duration between the last broadcast and the last reception of a message).
Vehicle context v is described by a list of vehicle context information, such as the driving direction, distance to the last forwarder, current number of reachable neighbor nodes, and distance to adjacent nodes road type.
Information context i is specified by the time of day, purpose of traveling, distance to the source, information accuracy, information category, news value, and change rate of the information.
The work in [7], also presents a new algorithm for a back-off counter. A number R is randomly chosen over the interval [0, CWbb], where CWbb represents the current contention window based on the benefit value, by:
Then, the back-off counter value BTimer is obtained by:
where the slot time is 13μs in the vehicular network.
3. The Enhanced Message Priority Mechanism
In this section, we describe the EMPM. As can be seen in Fig. 1, the EMPM is a cross layer architecture that combines the application layer and the MAC layer.
Recall that the EMPM consists of the benefit-value algorithm and the CW selection algorithm. The objective of the benefit-value algorithm is to calculate the benefit value of a message, which reflects the context of vehicular networks. The back-off counter selection algorithm modifies the IEEE 802.11p MAC by including the benefit value for the determination of the back-off counter value. To alleviate the impacts of frame collision between the messages with different priorities, we chose the back-off counter value according to the Poisson distribution instead of the uniform distribution.
Fig. 1 illustrates the structure of the EMPM in detail. Upon reception of a message from the higher layer, the EMPM calculates the benefit value based on the many parameters obtained from the vehicle. This benefit value is delivered in the MAC layer with the message. In the MAC layer, the message is first stored in the appropriate priority queue based on its class. Here, we assume that the position of new message in the priority queue is determined so that the order of the benefit values is maintained. If a message is ready to be transmitted by the channel, the back-off counter selection algorithm chooses a suitable value for the back-off counter.
3.1 Benefit-Value Algorithm
The benefit value of a message should be determined in such a way that it reflects the desired characteristics of vehicular networks, such as altruistic, sustainable, flexible, and scalable. Note that there are many parameters used to describe the context of a message, which is classified into the vehicle context and the information context [6]. From among these parameters, we focus in this section on a few key parameters of vehicular networks (i.e., vehicle speed, deceleration, message lifetime) and other (miscellaneous) factors. Given a message m from the higher layer, the benefit value β(m) of a message can be represented by:
For each parameter in (4), we will describe how we selected the weight factor and the function bi in the following sections.
3.1.1 Sensor function
Before calculating the message benefit value, we should consider the information from the sensor. A sensor is a converter that measures a physical quantity and converts it into an electrical signal. If a sensor detects a dangerous situation in the road environment, then it notifies the other vehicles of this information.
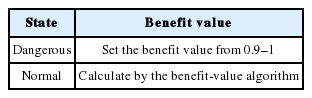
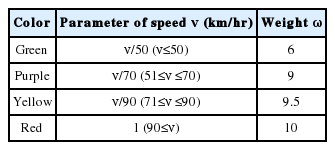
In this paper, we simply classify the driving situation into the two categories of a dangerous situation and a normal situation. If a vehicular sensor detects a dangerous situation, the benefit value will be a high value (e.g., randomly chosen over the interval [0.9, 1]), in order to give a higher priority to the messages containing important and urgent information. Otherwise, the benefit value is calculated by the benefit-value algorithm in Eq. (1). Table 4 summarizes the benefit value of the sensor function for the two different situations.
3.1.2 Speed function
A car driving at a higher speed may have a higher probability of getting into a traffic accident. This is because the driver, who is moving at a high speed, may not have enough time to react to the dangerous situation. To alleviate this problem, most countries set speed limits to regulate the speed of moving vehicles. Fig. 2 illustrates that 62% of all countries have a speed limit that is less than or equal to 50 km/hr. As can be seen in Fig. 2, we consider vehicles driving at speeds in excess of 50 km to have the higher probability of getting into an accident. In order to differentiate between the two speeds (Fig. 2 green and other colors), we assume that a large gap exists between the weight values of green and other colored speeds. We also assumed that few differences exist between the weight values of speeds higher than 50 km/hr (color coded red, yellow, and purple). According to the experiment that was based on the above assumptions, the benefit value of the speed function is defined as shown in Table 5.
3.1.3 Deceleration function
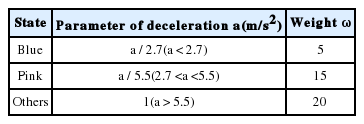
In this work, we also considered another important factor—the deceleration of a vehicle. Once a driver recognizes a dangerous situation, he/she usually decelerates the speed of his/her car. Therefore, deceleration can be a good indicator for representing an urgent traffic incidence. In this paper, we followed the settings in [14]. If the absolute value of deceleration is less than 2.7 m/s2, the driving situation is interpreted as a normal situation. When it is between 2.7 m/s2 and 5.5 m/s2, the proposed algorithm gives more weight to its messages. Finally, if it exceeds 5.5 m/s2, the highest weight values are assigned to the messages. Table 6 shows the resulting weight assignments of the deceleration function.
3.1.4 Message life function
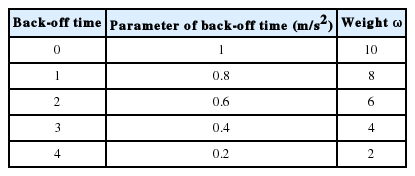
In a vehicular network, the message should be transmitted in a timely manner. However, if a packet collision happens, the message will be delayed over a long period of time. Then, the importance of the message will be affected by the collision. If a collision occurs, the important messages are sent immediately. As such, it is necessary to have a shorter back-off time and reduce the impact of the delay caused by the collision with a larger weight message. Table 7 shows the values of the lifetime function.
3.2 Back-off Counter Selection Algorithm
In the contention-based IEEE 802.11 standard MAC protocol, there are two key parameters used for differentiating the quality of service of a message, which are the IFS and the CW size. In this section, we present an alternative approach, called the back-off counter selection algorithm, for the determination of a back-off counter value depending on the benefit value.
The basic idea of the back-off counter selection algorithm is to utilize the Poisson distribution. The Poisson distribution is a discrete probability distribution that expresses the probability of a given number of events occurring in a fixed interval of time. It can also be used for the number of events in other specified intervals, such as distance, area, or volume. Assume that in our work, every slot can be the interval of time. First we must define the random variable of X for the back-off counter value. Then, the probability density function (PDF) of the Poisson distribution is given as follows:
where the parameter λ is a function of the benefit value β(m). Note that, to reduce the delay of the high priority messages, this function must be a non-increasing function of the benefit value β(m). To meet this requirement, we employed the following function for obtaining the value of parameter λ:
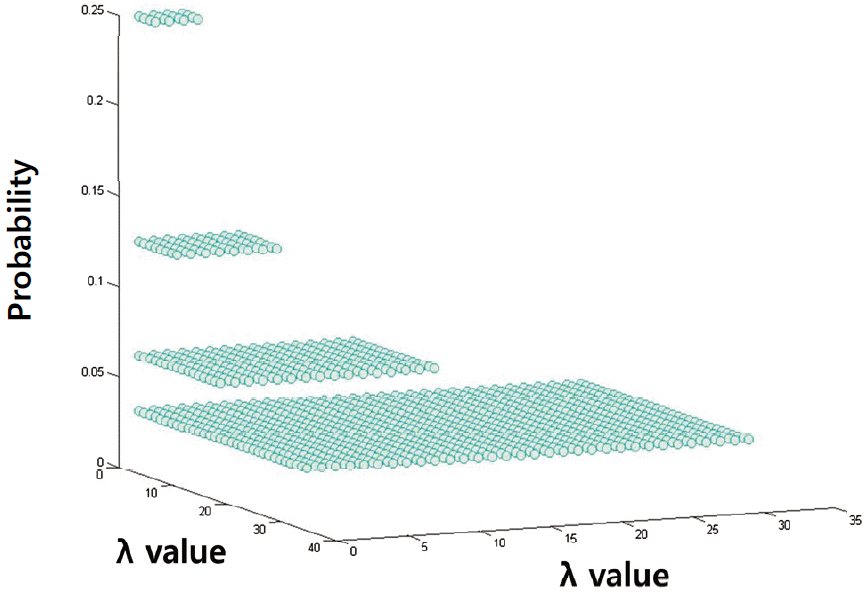
Figs. 3 and 4 show the probability of a packet collision occurring between two vehicles. If the contention window is equal to 4 the collision probability is equal to 0.25 when the contention window is chosen randomly. However, the collision probability of the Poisson distribution is based on the parameter of λ. In Fig. 3, the highest probability is 0.3085 when the λ is equal to 1. After that, the result is lower than 0.25. That means the two vehicles may have less chance to get into a collision because of the different parameters.
When MB is less than 20, we still use the Poisson distribution shown in Fig. 5. If there is a collision, the contention window will be doubled. The next contention window will be 2MB. The probability of the message, which is based on the Poisson distribution with the parameter of MB, is as follows:
This is the next probability of the message with the 2MB.
And then we can compare the peak points of the two distributions. According to the algorithm of the 802.11p in the MAC layer, the peak points of the two distributions are the P(MB) and P(2MB):
The division of the two points is as shown in Eq. (11).
So, if the contention window is doubled by the EMPM, the probability of the peak point will be lower than before. In other words, the probability function would be flatter than the previous one and there is a high probability that the other number is chosen. In that case, the result can be seen in Fig. 6.
If the MB is equal to or lager than 20 and there still be a collision, it needs to be quickly made flat.
Let’s assume that the cumulative distribution function of the Poisson distribution is:
And the characteristic root of the distribution is as shown in Eq. (15).
So the characteristic root with the value of MB can be obtained in our mechanism.
Using the Taylor formula to simplify the equation, the formula is as shown in Eq. (20).
By ignoring the little parameter from the fourth term, we can get the results shown in Eq. (22).
The characteristic function provides an alternative way for describing a random variable. As we know, there is an alternative way for describing the random variable. The characteristic function is similar to the cumulative function.
The characteristic root of
In this case we can use the Gaussian distribution instead of the Poisson distribution. In Fig. 6, we can visually observe the results, which show that the Poisson distribution is close to the Gaussian distribution.
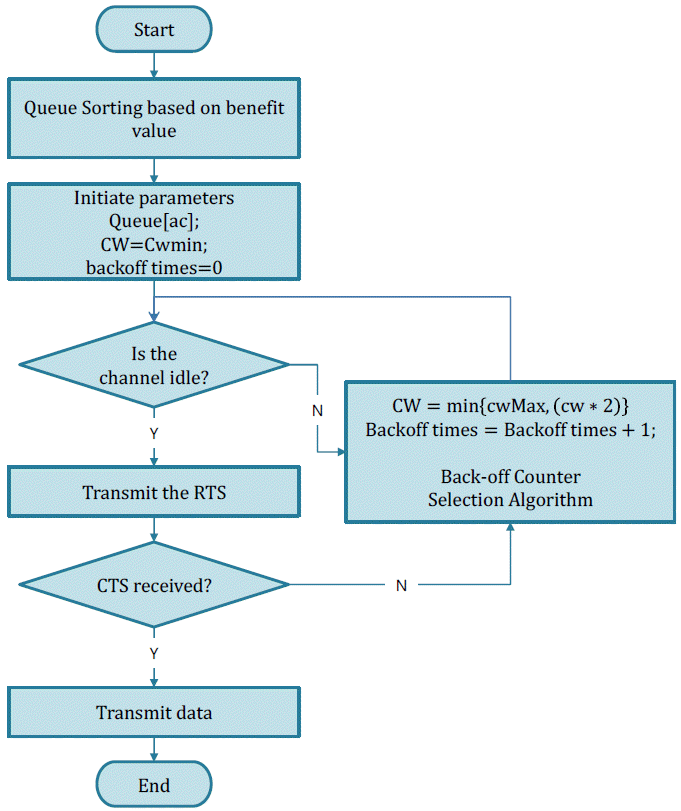
Fig. 7 is the flow chart of the MAC layer. We modified the CSMA/CA mechanism by adding the back-off counter selection Algorithm. As previously described, the benefit value is transmitted to the MAC layer with the message from the higher layer. When trying to send a message that has been received, after creating the packet, we initiated the transmission and obtained the priority queue. Then we sorted the queue according to the benefit values. At this time the queue is an enhanced priority queue with the benefit value. Compared with the traditional algorithm, the improved mechanism sorts the queue first and it input some initial parameters, which are standard in the 802.11p. If the channel is idle, the message will be sent. If the channel is not idle, we doubled the contention window and added the back-off times.
Algorithm 1 shows the back-off counter selection algorithm, which handles the contention window by using the EMPM mechanism. At the beginning of the algorithm, the parameters should be initiated and the benefit value β(m) can be received from the upper layer. If the contention window is larger than 20, as we proved before, the Gaussian distribution should be used. What’s more, we also add the back-off times in the variance part because we wanted to make the peak point lower and to flatten the probability curve. If the contention window is less than 20, the Poisson distribution will be applied to this part.
4. Performance and Results
In this section, we use Veins, SUMO, and OMNet++ to simulate the mechanism and compare our scheme with other existing schemes. In paper [15], authors developed a hybrid simulation framework, Veins (Vehicles in Network Simulation), composed of the network simulator OMNeT++ and the road traffic simulator SUMO.
We also describe the simulation setup that we used in our performance evaluation tests. The setup includes a network simulator, a road traffic simulator, and real world maps. The OMNeT++ network simulator is used with the MiXiM framework. OMNeT++ is a modular network simulation framework that uses components written in C++. MiXiM is an extension to OMNeT++ that provides a simulation environment for mobile wireless networks. To ensure that the traffic is representative of real world traffic for each of the test cases, we used real world maps from SUMO.
There are four priority queues, but it is hard to distinguish between the different types of messages in the simulation. Therefore, the message is sent to a random priority queue. After that, we calculated the results by the value-benefits. The value-benefits indicate the sum of benefits received by each node. If the value-benefits are high, important and urgent messages are received. Another metric is the total value-benefits, which indicates the sum of total benefits obtained in the whole network.
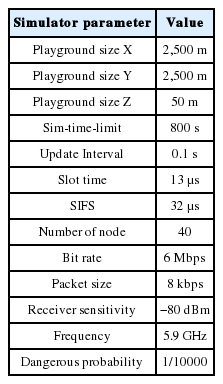
The simulation square is 2,500×2,500 m2. For every 0.1 second the system will be refreshed and will recalculate the environment factors. Forty nodes were calculated in our simulation. The data rate was set for 6 Mbps. The packet rate was 40 packets per second. The message could then be transmitted at most 3 hops. The size of the packet was 8 kbps and the length of the queue was 30. The parameter settings in the simulation are summarized in Table 8.
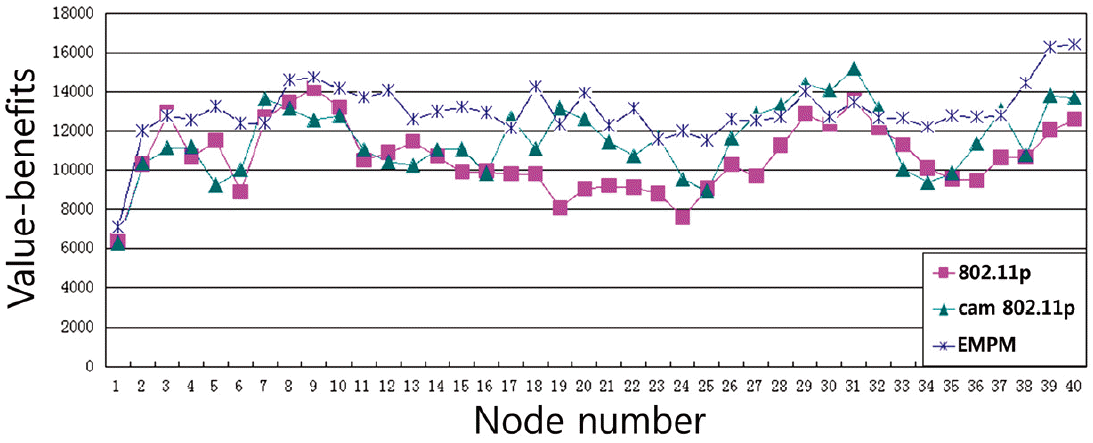
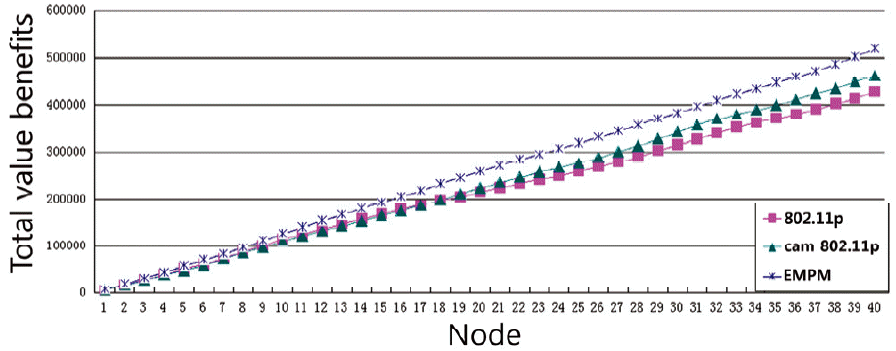
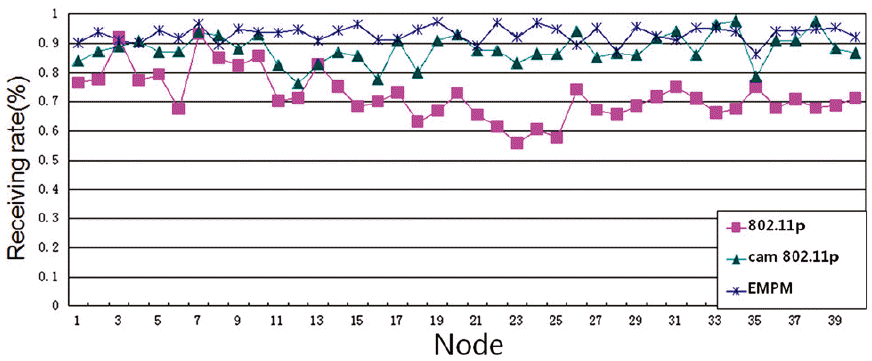
In Fig. 8, we can see that the total value-benefits of EMPM are better than the others. Compared with traditional 802.11p, the CAM-802.11p also improved the total value-benefits. In Fig. 9 we added the benefit value for every five nodes and in Fig. 10 we calculated all of the nodes of the scenario. In the Figs. 11–13, we compared the three different kinds of situations. We calculated the receiving rate when the total benefit-value is larger than 0.9, 0.7, and 0.5 respectively.
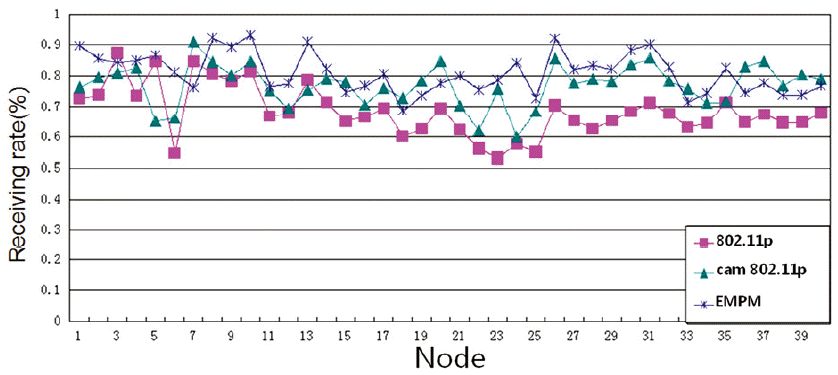
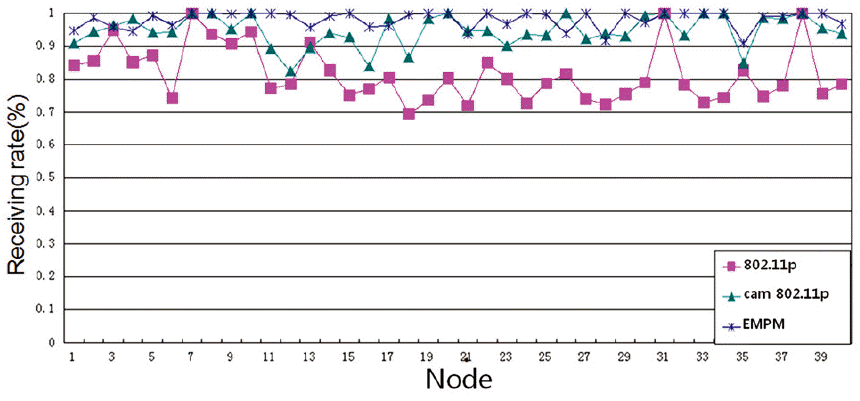
From Fig. 11, we can see that the EMPM is close to 97% of the maximum receiving rate if the benefit value is larger than 0.9. As shown in Fig. 12, if the benefit-value is larger than 0.7, the EMPM is still good. However, as shown in Fig. 13, if the benefit value is larger than 0.5, our algorithm is similar to the other algorithms. As a result, we can see that our mechanism is much better if the benefit value is close to 1, as it means that most of the important messages were received.
As shown in Fig. 11, the CAM-802.11p model is better than the 802.11p. The receiving rate of CAM-802.11p is about 80%. Although it improves the receiving rate, it is still not good enough.
Furthermore, if the benefit value is larger than 0.5, our algorithm is similar to other algorithms in Fig. 13. From Figs. 11–13, we are able to conclude that the receiving rate of EMPM is better than the other two methods when the benefit value is large enough.
In Fig. 14, we calculated the receiving rate of the first priority in which the benefit value is larger than 0.9. The message in the first priority queue means that it is important. In addition, if the benefit value is larger than 0.9, this represents the most important message in the system. For some nodes, the receiving rate can be 100% by EMPM. As shown in Fig. 14, the EMPM is better than other algorithms in terms of receiving rate.
As show in Figs. 15–17, the average packet delay is calculated in the simulator. In Fig. 15, the average packet delay is counted when the benefit value of the message is larger than 0.9. The delay of the EMPM is the lowest one, which means that the packet delay is brief when the packet is important.
In Fig. 16, the average packet delay is calculated with the benefit value of the message, which is larger than 0.7. In this case the packet delay of the EMPM is between 3–15 ms. It is better than CAM-802.11p and 802.11p. The packet delay of the 802.11p model is between 40–60 ms.
In Fig. 17, the average packet delay is calculated with the benefit value of the message, which is larger than 0.5. In this case, the packet delay of the EMPM is close to other two methods. As the benefit value decreases, the EMPM delay increases.
We can conclude from the simulation results that the EMPM improved the total value benefits and the receiving rate. This means that when considering the environment of the real world, more important and urgent messages can be sent successfully and quickly.
5. Conclusion
In this paper, we have proposed an enhanced priority mechanism for the vehicular network by applying the benefit value and the Poisson distribution. Some of the important factors in a real world environment, such as the speed and the deceleration should be taken into account. We proposed the EMPM with the benefit-value algorithm to calculate the benefit-based priority of the messages. Based on the MAC layer of 802.11p, we also proposed the back-off counter selection algorithm. In comparison with different mechanisms using OMNET++ the total benefit value is improved by 20%. In the first priority queue, the receiving rate of most messages, whose benefit value is larger than 0.9, can be above 95%. Even some of the receiving rates can be 100%. The EMPM can have less of a delay when the benefit value is large.
In this paper, we did not consider the multi-channel situation. There are seven channels in the vehicular network of 802.11p. For future work, we plan to design a new protocol reflecting the real word factors in different channels.
Acknowledgement
This work was supported by a two-year Research Grant from Pusan National University.
References
Biography
Chang Liu
He received the B.S. degree in Computer Science from Northeastern University, Shenyang, China, in 2011, the M.S. degree in Institute of Logistics Information Technology, Pusan National University, Busan, Korea, in 2013. He is currently a member of staff with Ericsson, China. His research interests include vehicular networks.

Sang-Hwa Chung http://orcid.org/0000-0003-1329-1188
He received the B.S. degree in electrical engineering from Seoul National University, Seoul, Korea, in 1985, the M.S. degree in computer engineering from Iowa State University, Ames, in 1988, and the Ph.D. degree in computer engineering from the University of Southern California, Los Angeles, in 1993. He was an Assistant Professor with the Department of Electrical and Computer Engineering, University of Central Florida, Orlando, from 1993 to 1994. He is currently a Professor with the Computer Engineering Department, Pusan National University, Busan, Korea. His research interests are in the areas of embedded systems and wireless networks

Han-You Jeong
He received the B.S., M.S., and Ph.D. degrees in the Department of Electrical Engineering and Computer Science from Seoul National University, Seoul, Korea, in 1998, 2000, and 2005, respectively. From 2005 to 2007, he was a senior engineer with the Telecommunication R&D Center, Samsung Electronics, Suwon, Korea. In 2008, he joined the Digital Technology Center, University of Minnesota, Minneapolis, as a postdoctoral research fellow. He is currently an associate professor with the Electrical Engineering Department, Pusan National University, Busan, Korea. His research interests include wireless networks, vehicular networks, and optical networks.

Ik-Joo Jung http://orcid.org/0000-0002-1475-8846
He received the B.S. degrees in Computer Science Engineering from Pusan National University in 2013. He is currently Master student in the Computer Engineering Department, Pusan National University, Busan, Korea. His research interests include embedded systems and wireless sensor networks.